Integrating Snowflake with Azure AD via OAuth
Integrate Snowflake with Azure AD via OAuth—configure app registrations, scopes, and security settings to enable secure, role-based access.
1. Setting Up a Snowflake OAuth Resource in Azure AD
1.1. App registration for Snowflake OAuth resource
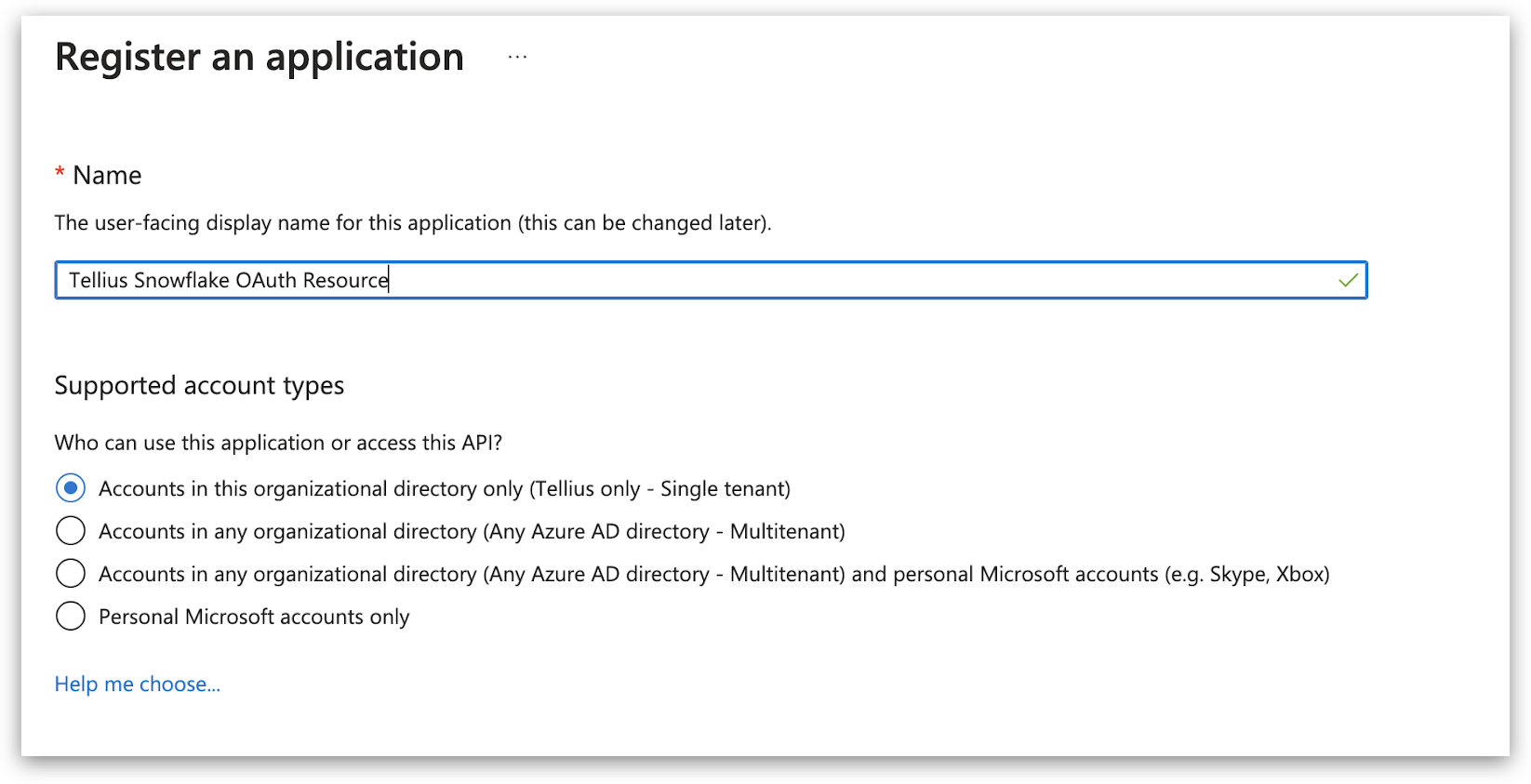
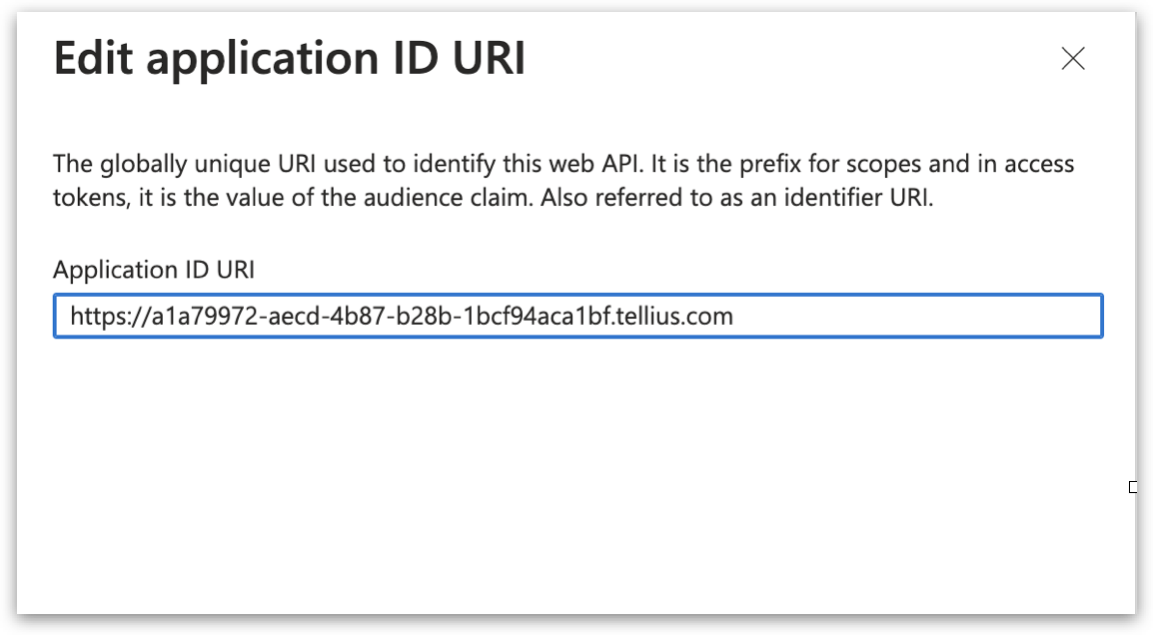
1.2 Modifying the API
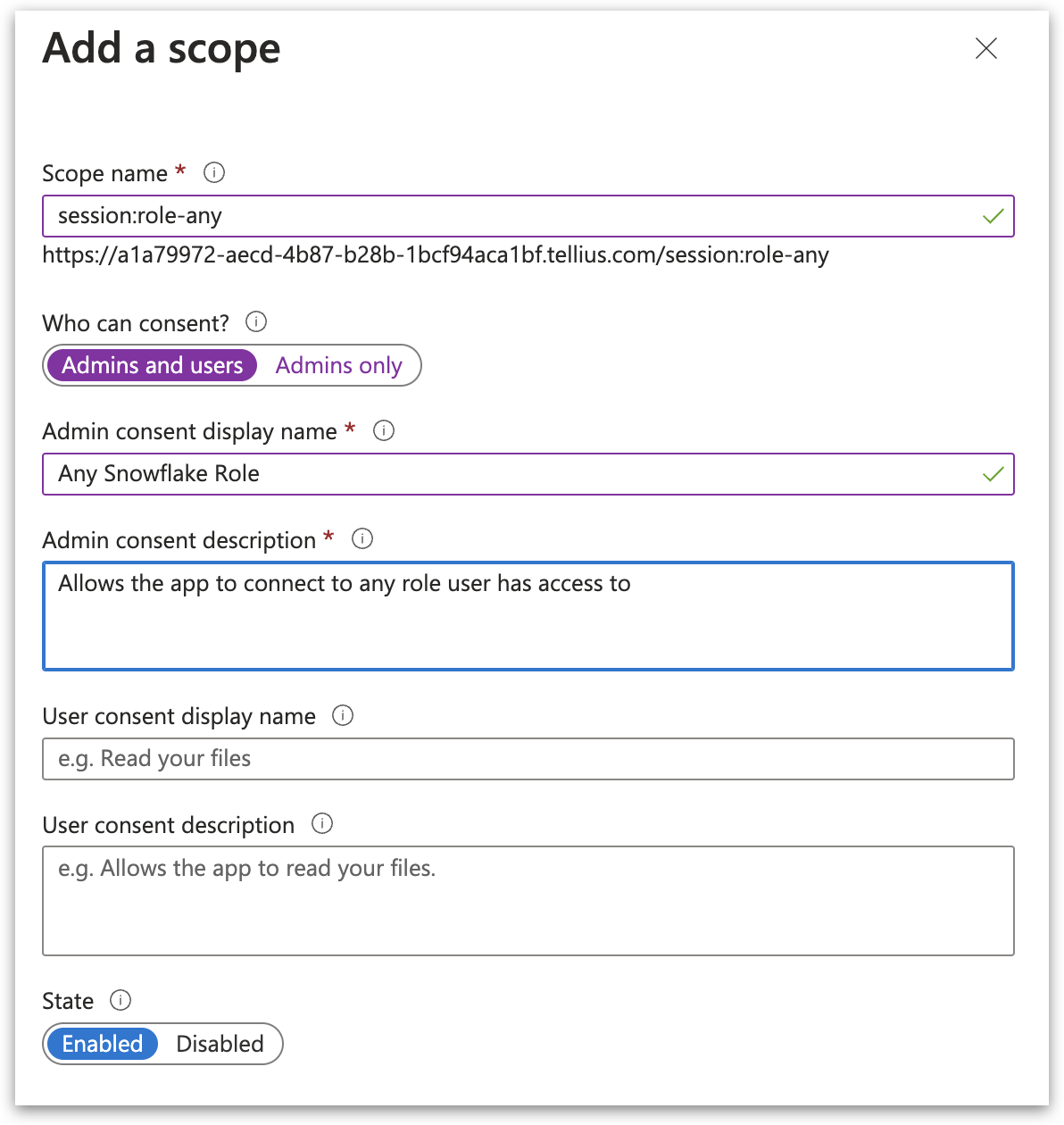
1.3 Adding a new scope
2. Creating a Snowflake OAuth Client App in Azure AD
2.1 App registration for Snowflake OAuth Client
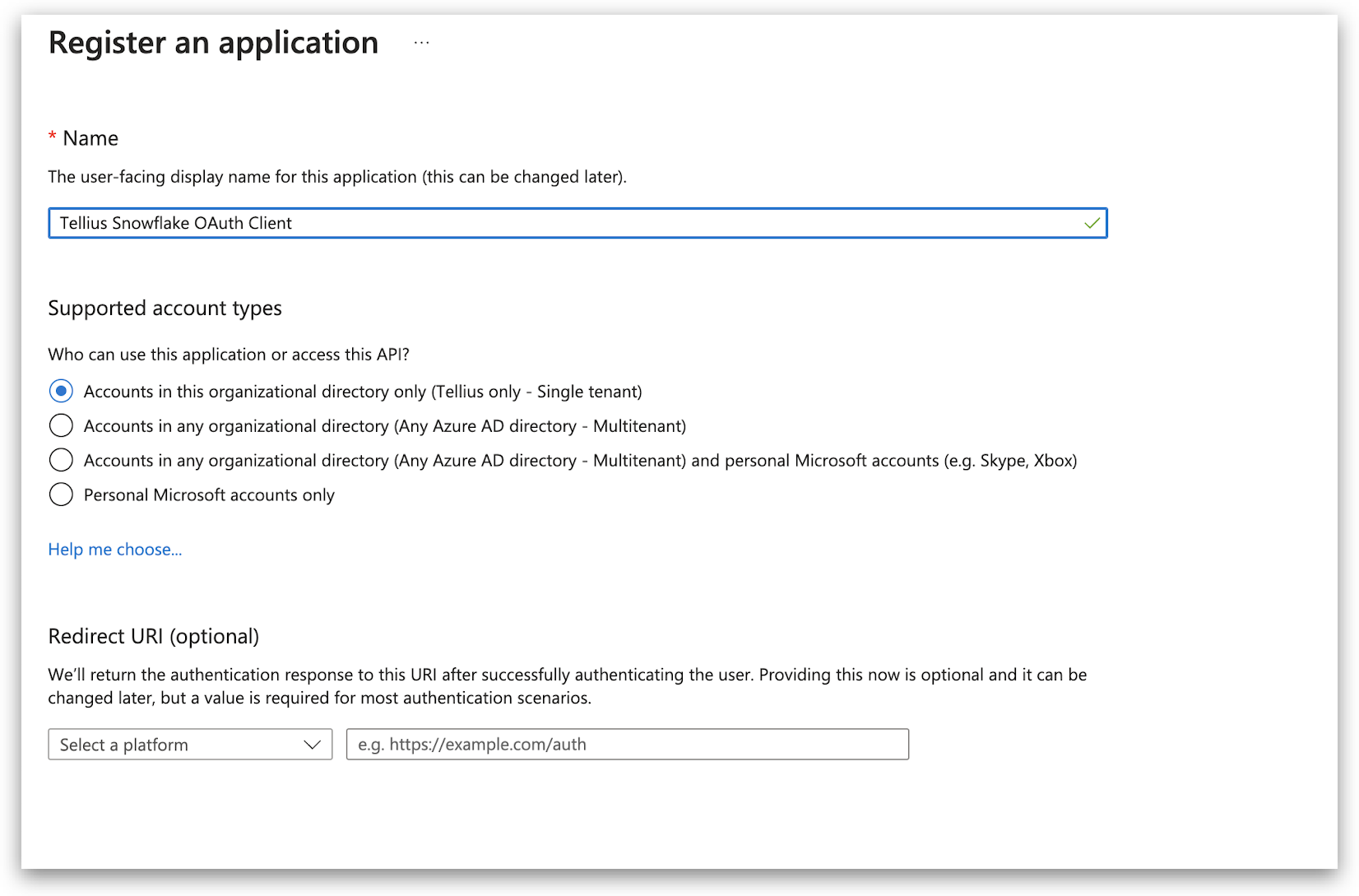
2.2 Setting up Authentication
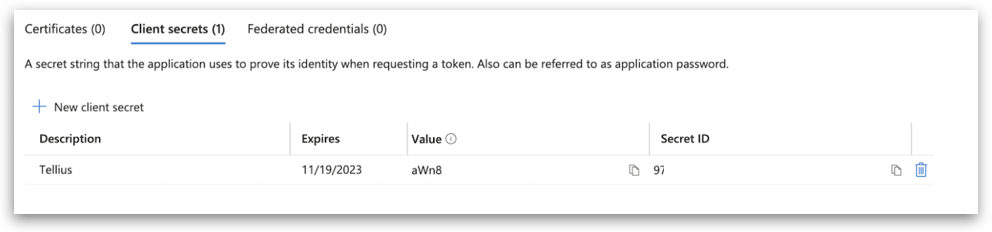
2.3 Generating Client Secret
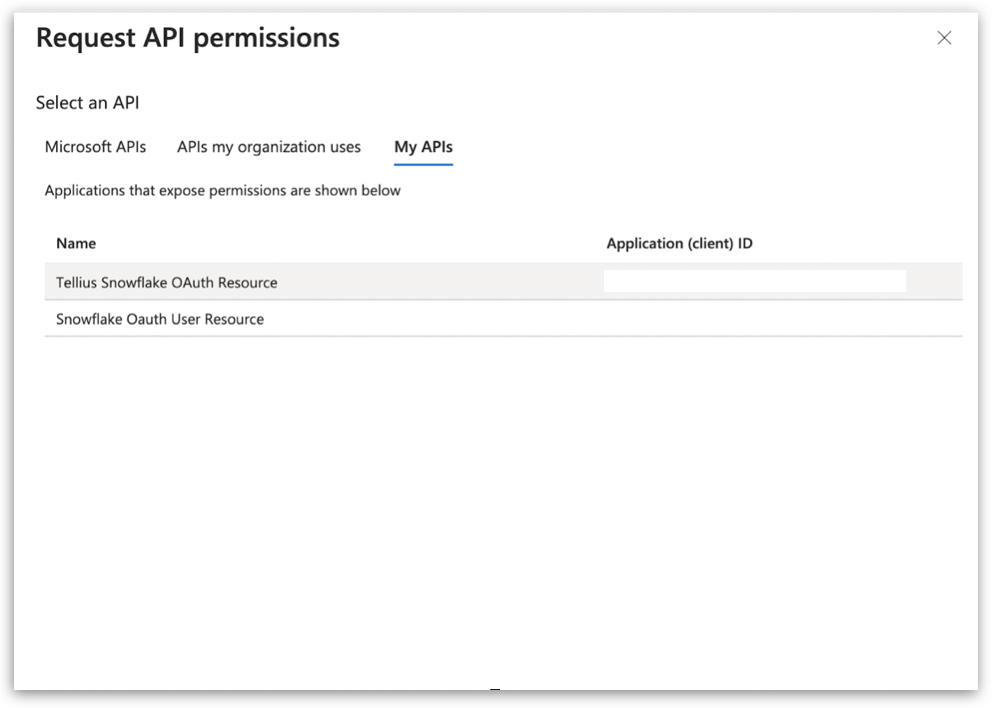
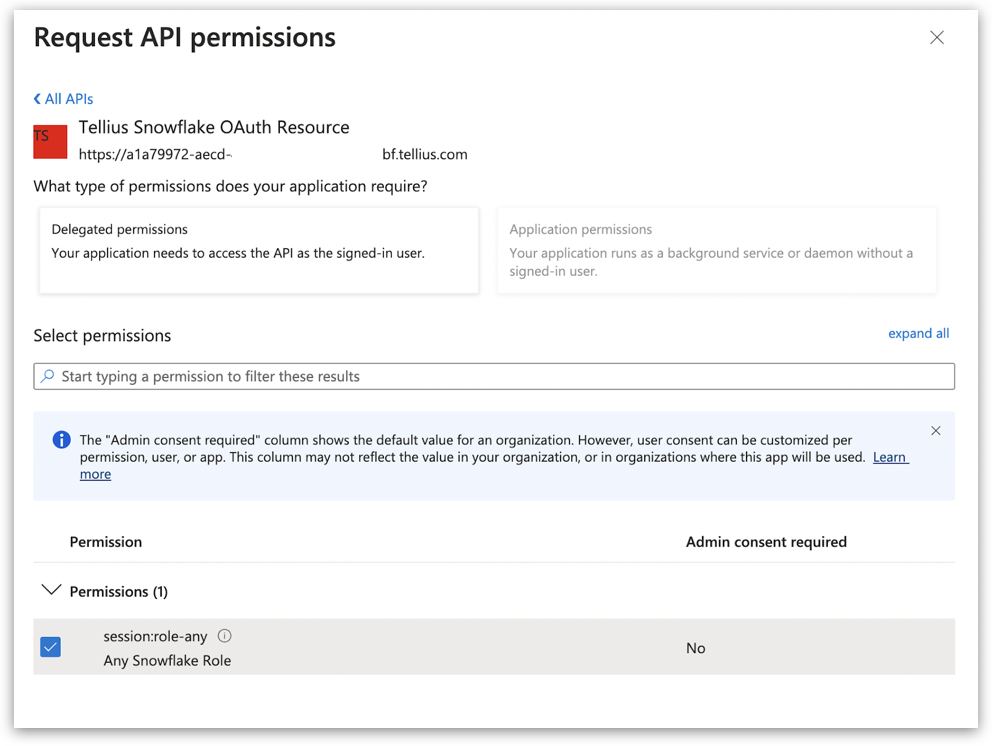
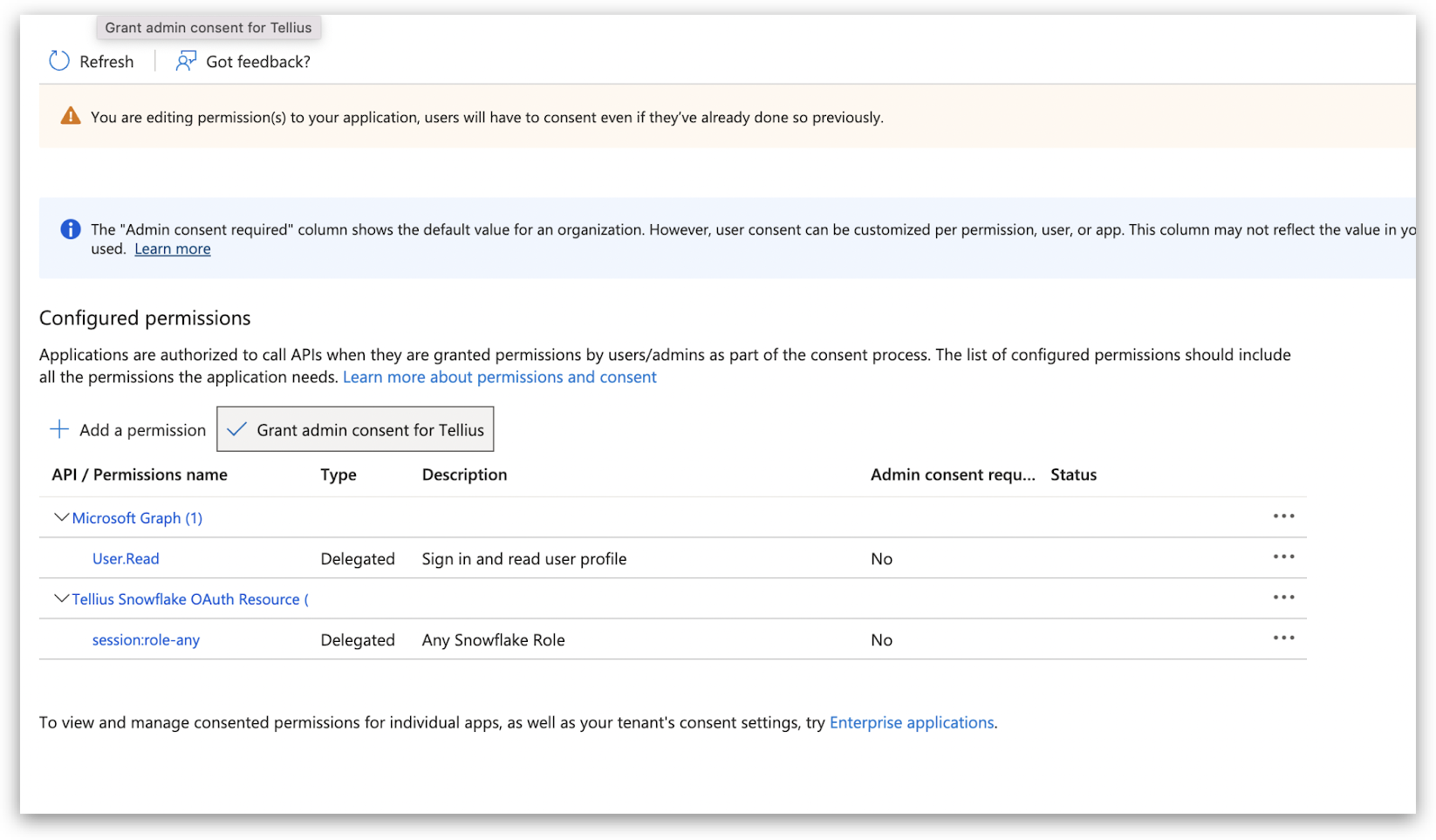
2.4 Defining API permissions
3. Collecting Azure AD OAuth Information
3.1 Accessing OAuth Details
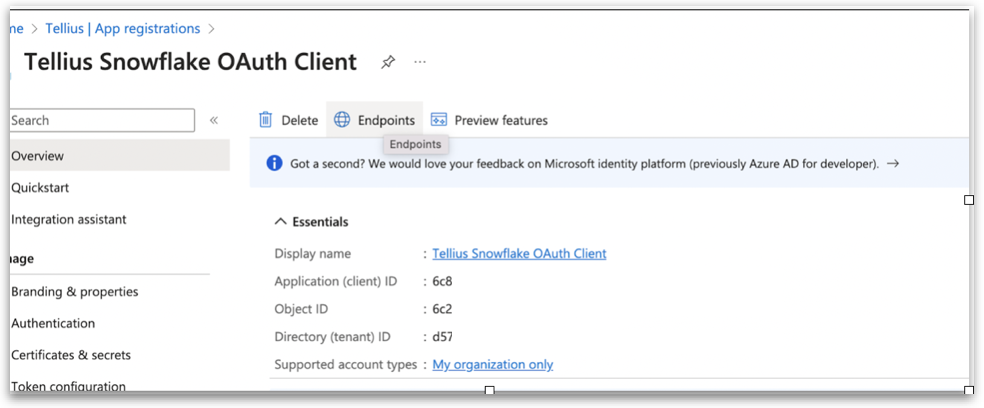
3.2. Gathering OpenID Connect Metadata
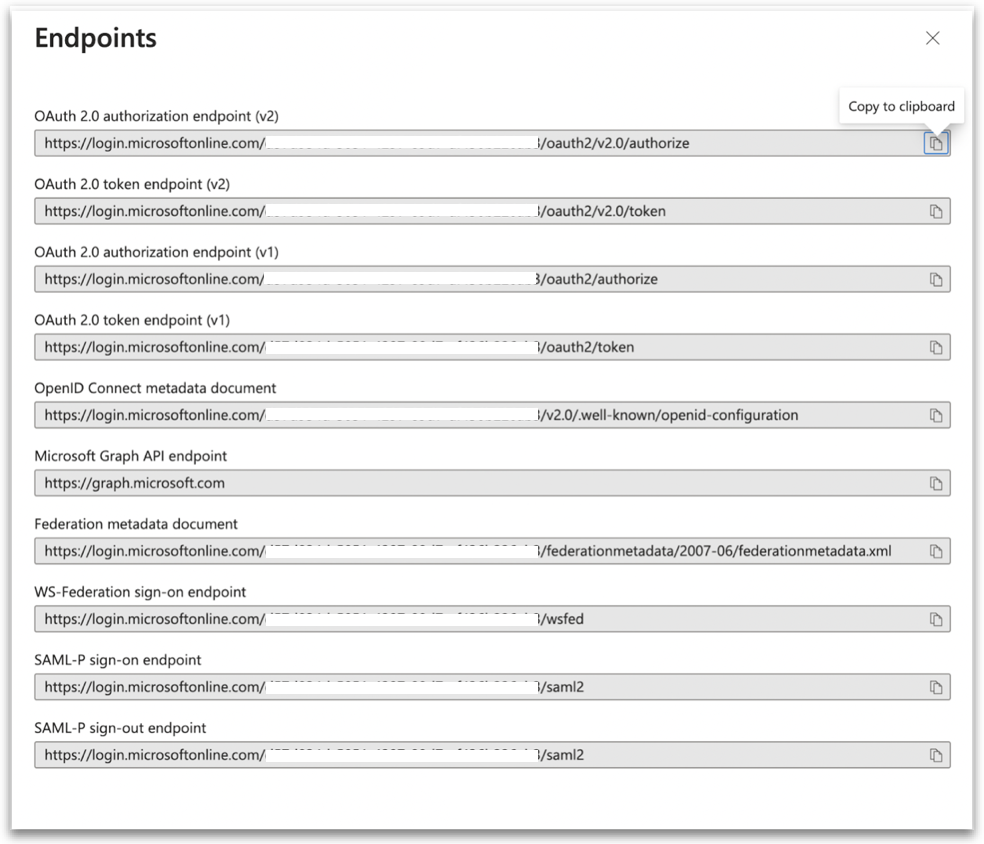
3.3. Fetching Federation Metadata
4. Configuring the OAuth Authorization server on Snowflake
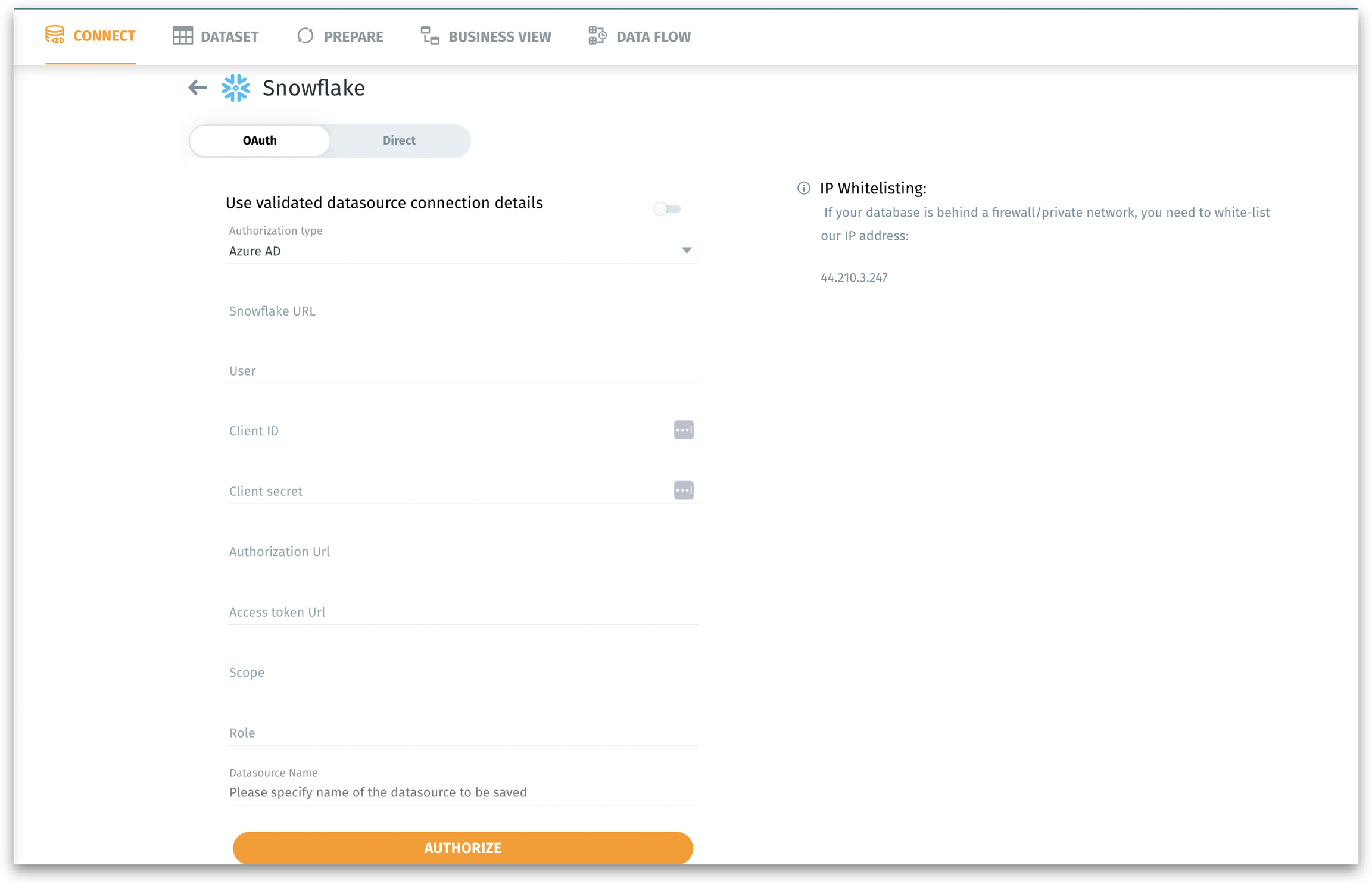
5. Configuring in Tellius
Was this helpful?