Azure PrivateLink
Integrate Snowflake with Azure Private Link in Tellius—configure private endpoints, DNS zones, and secure connections for enhanced data protection.
What is an Azure PrivateLink?
Pre-requisites
Setting up Snowflake
select SYSTEM$GET_PRIVATELINK_CONFIG() using role ACCOUNTADMIN;Create a Private endpoint in Azure
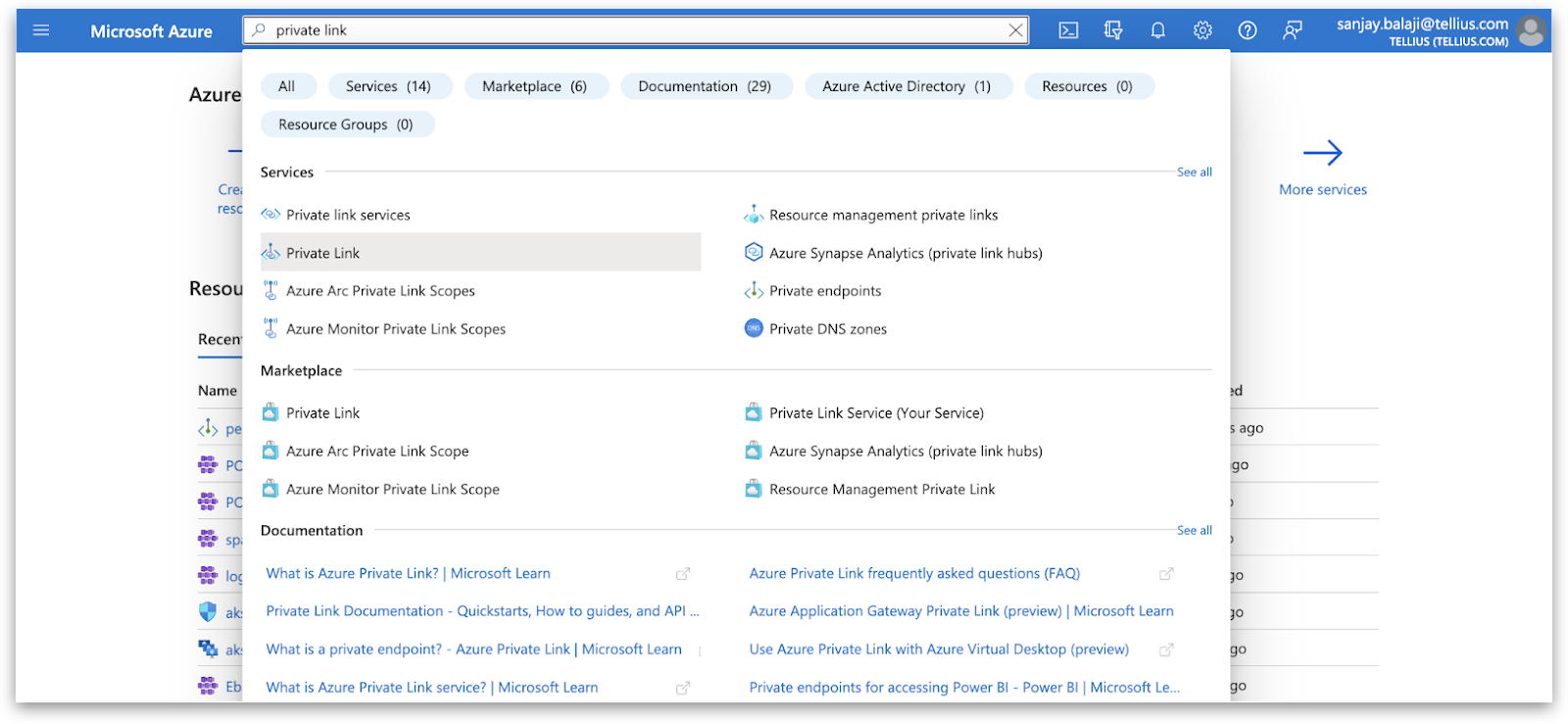
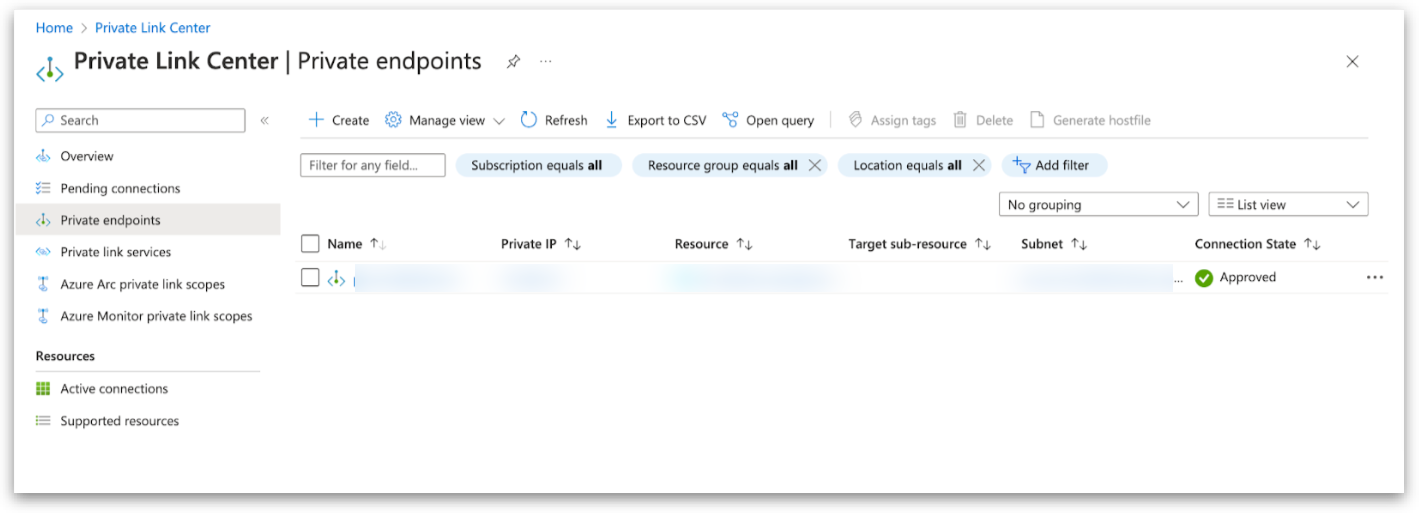
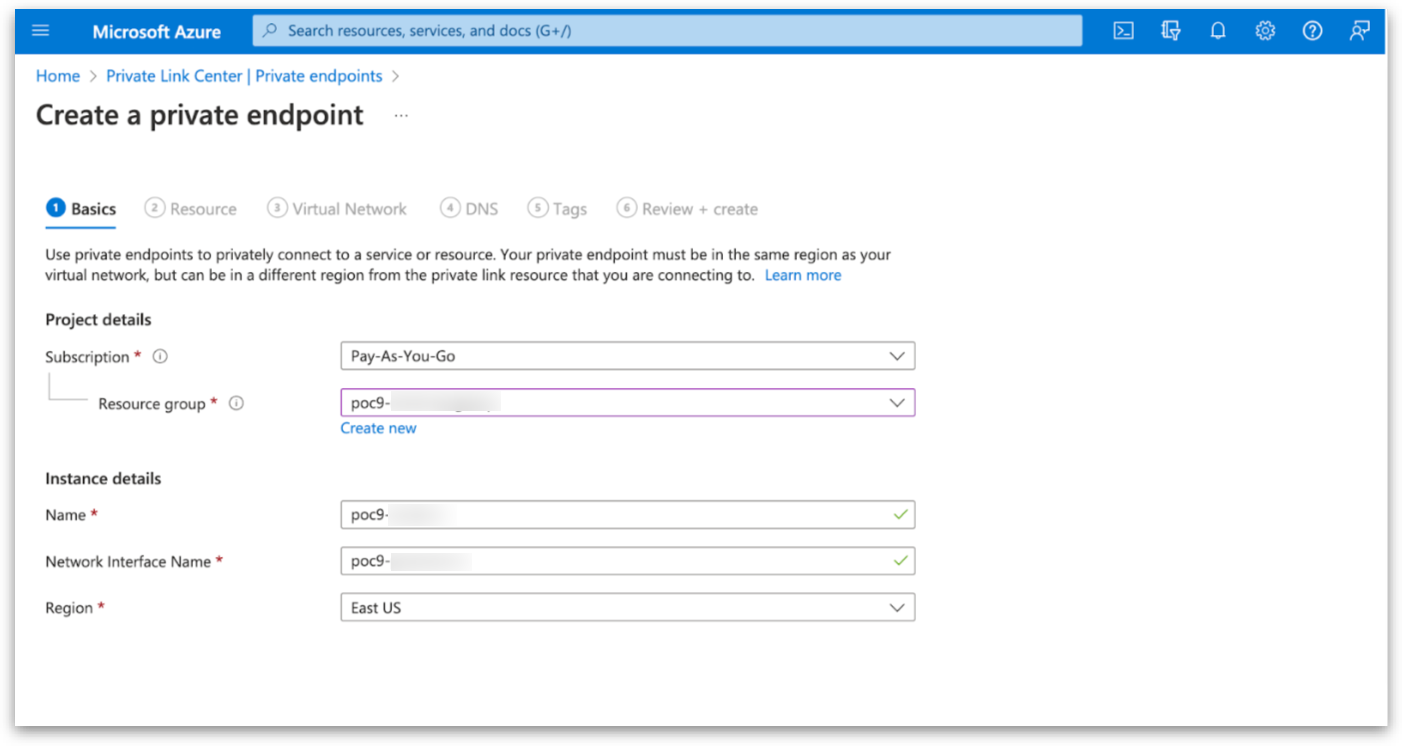
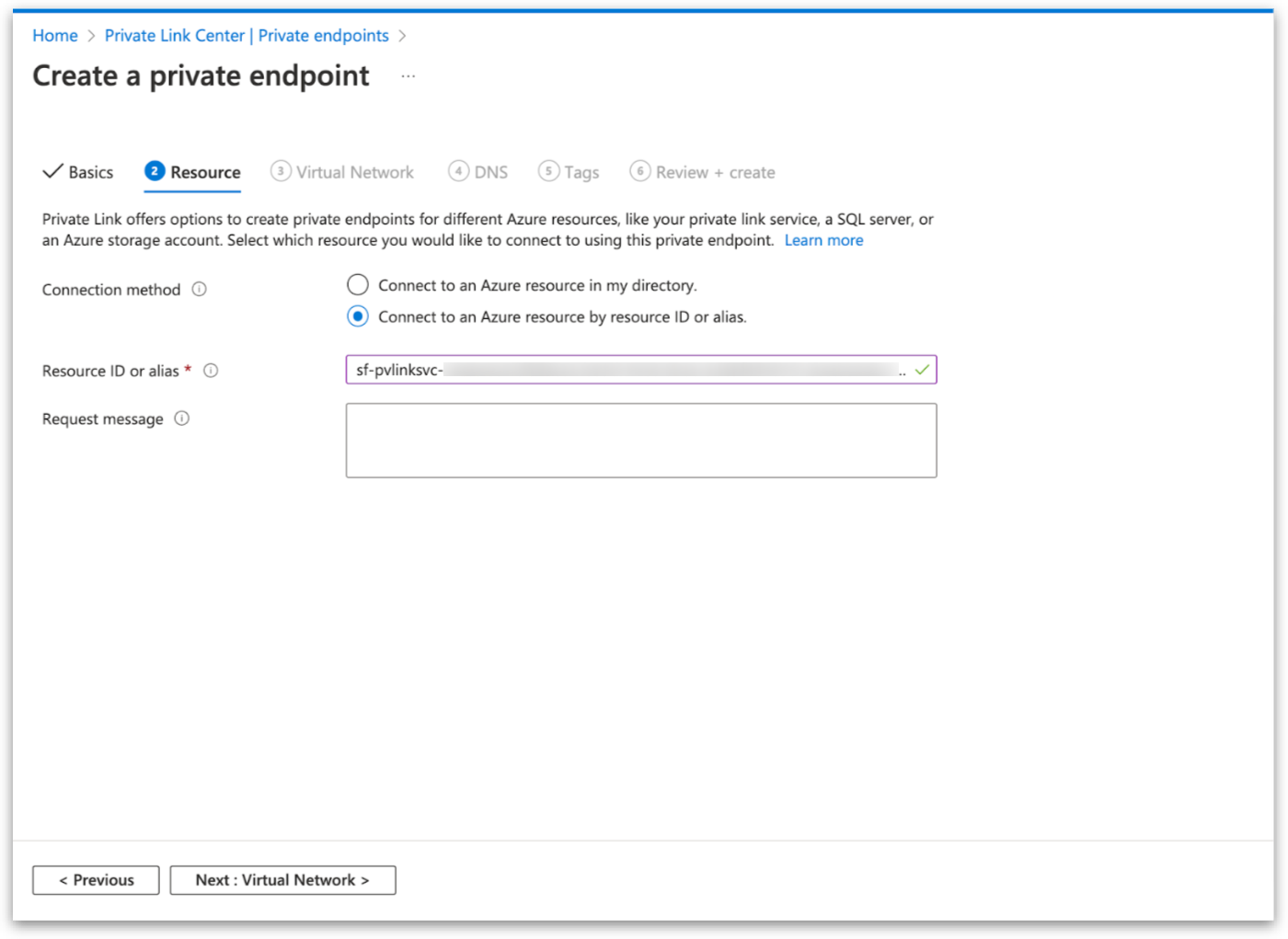
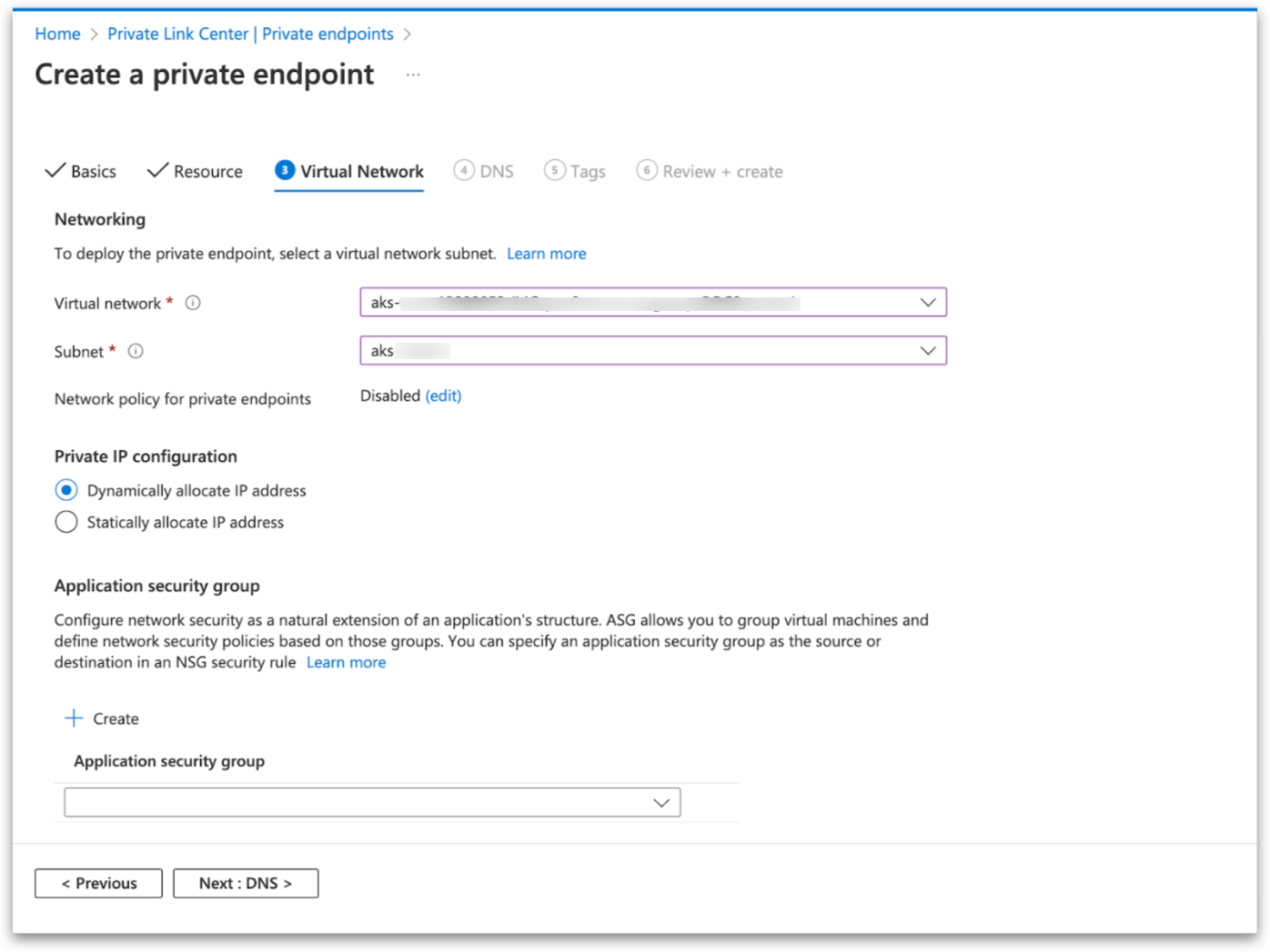
Obtain accessToken for Private Endpoint from Azure CLI
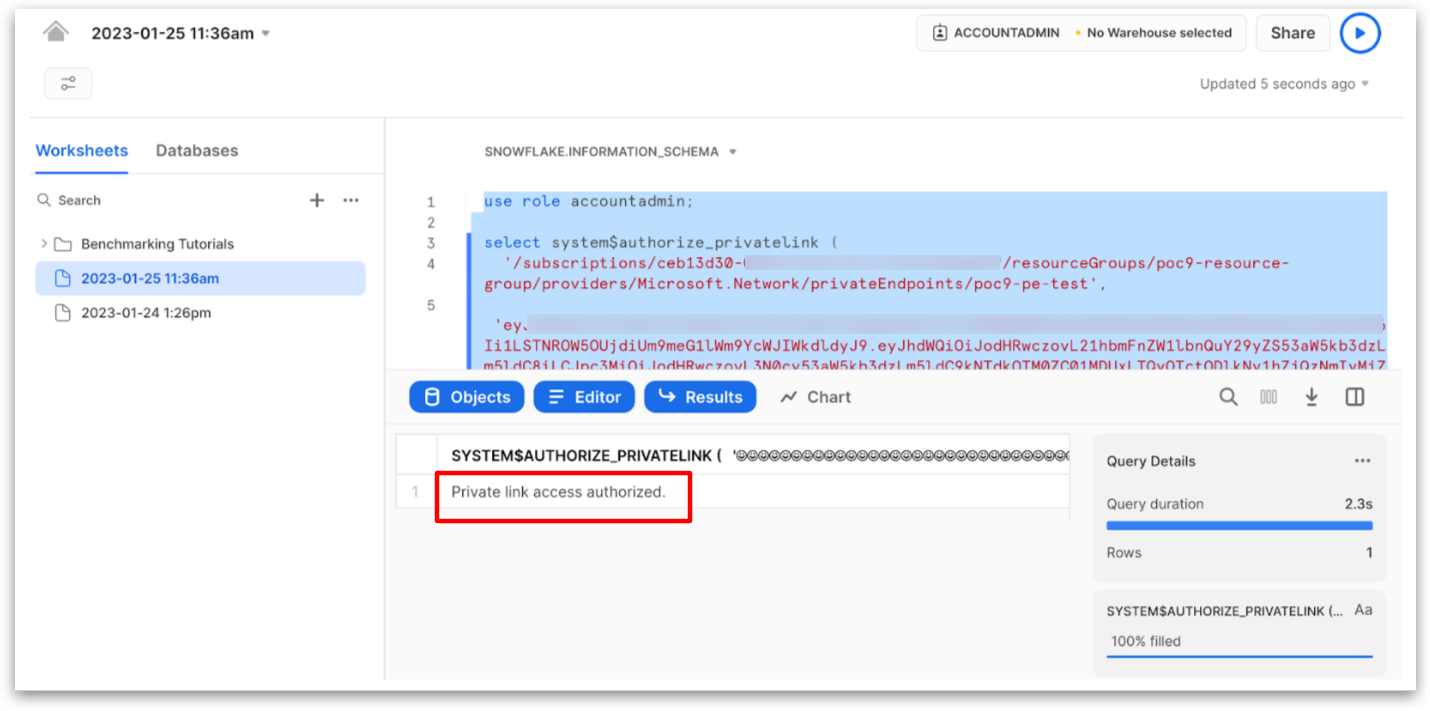
Authorize Private Link in Snowflake
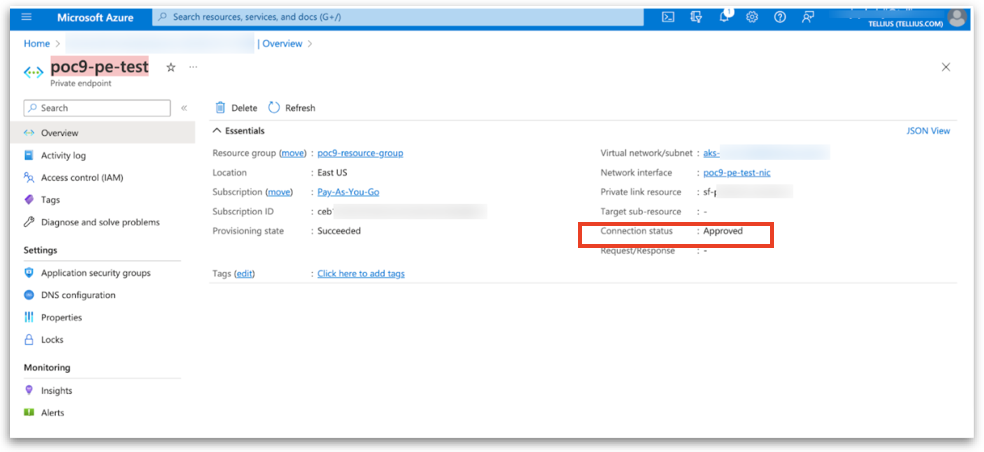
Approve Private Endpoint in Azure
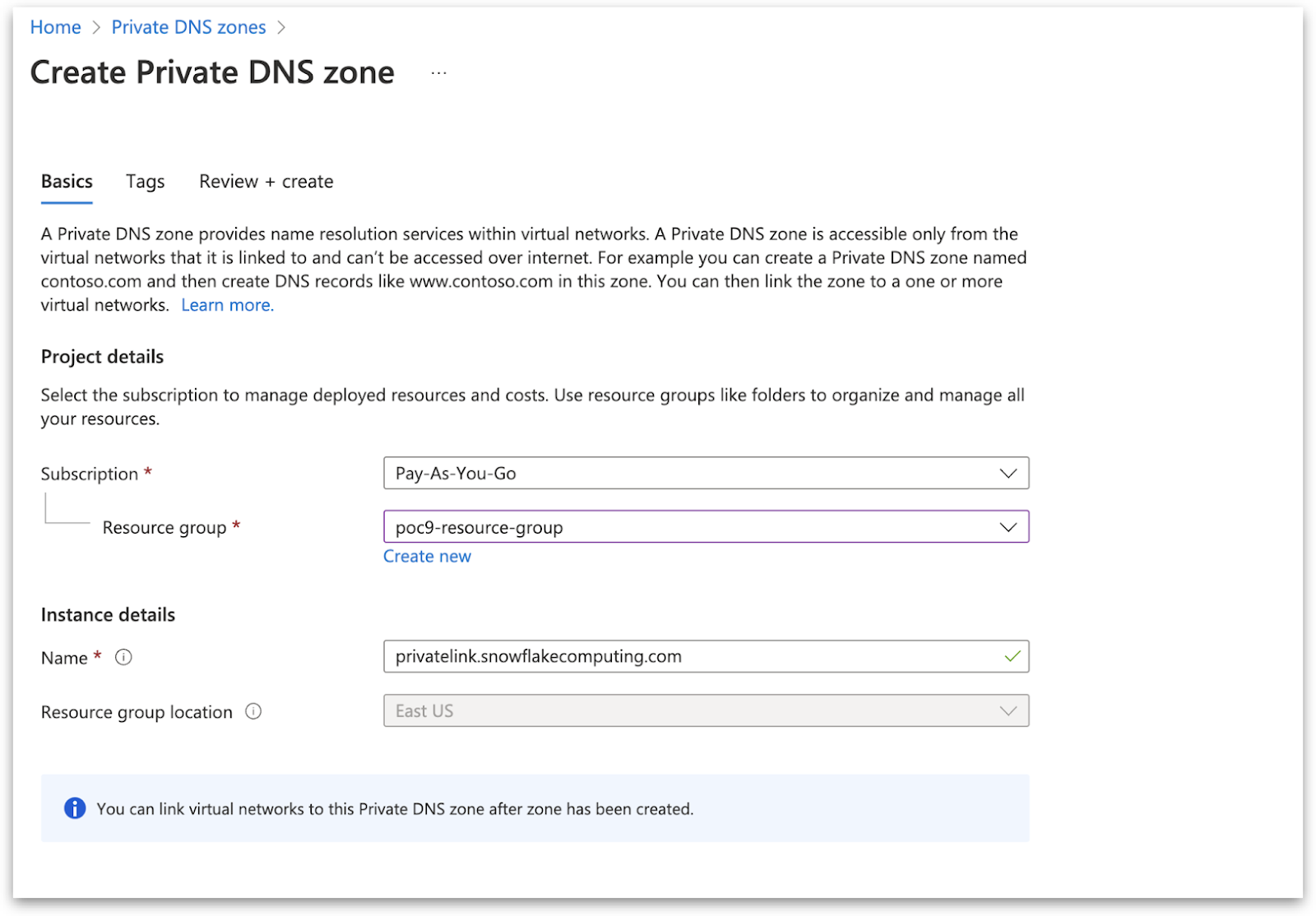
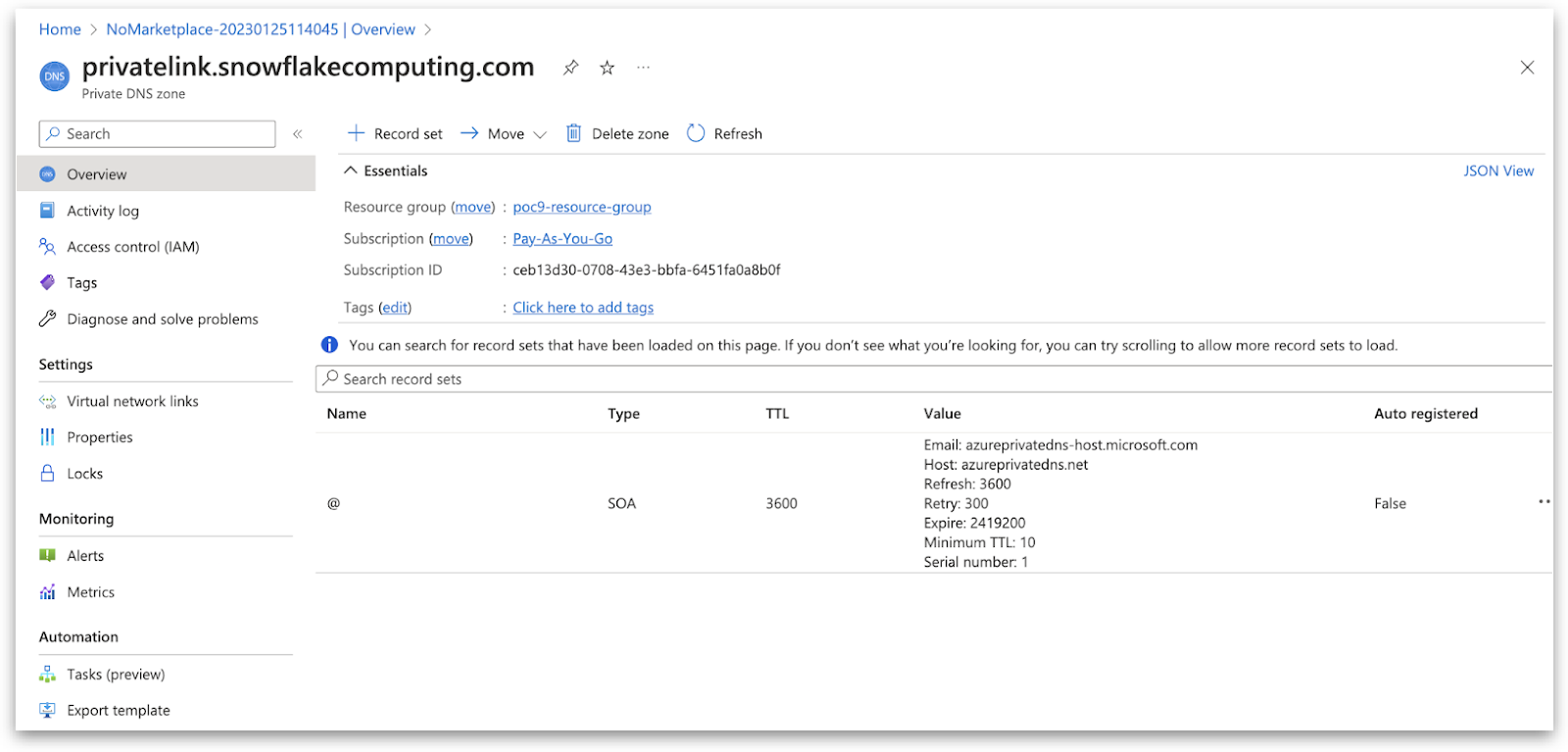
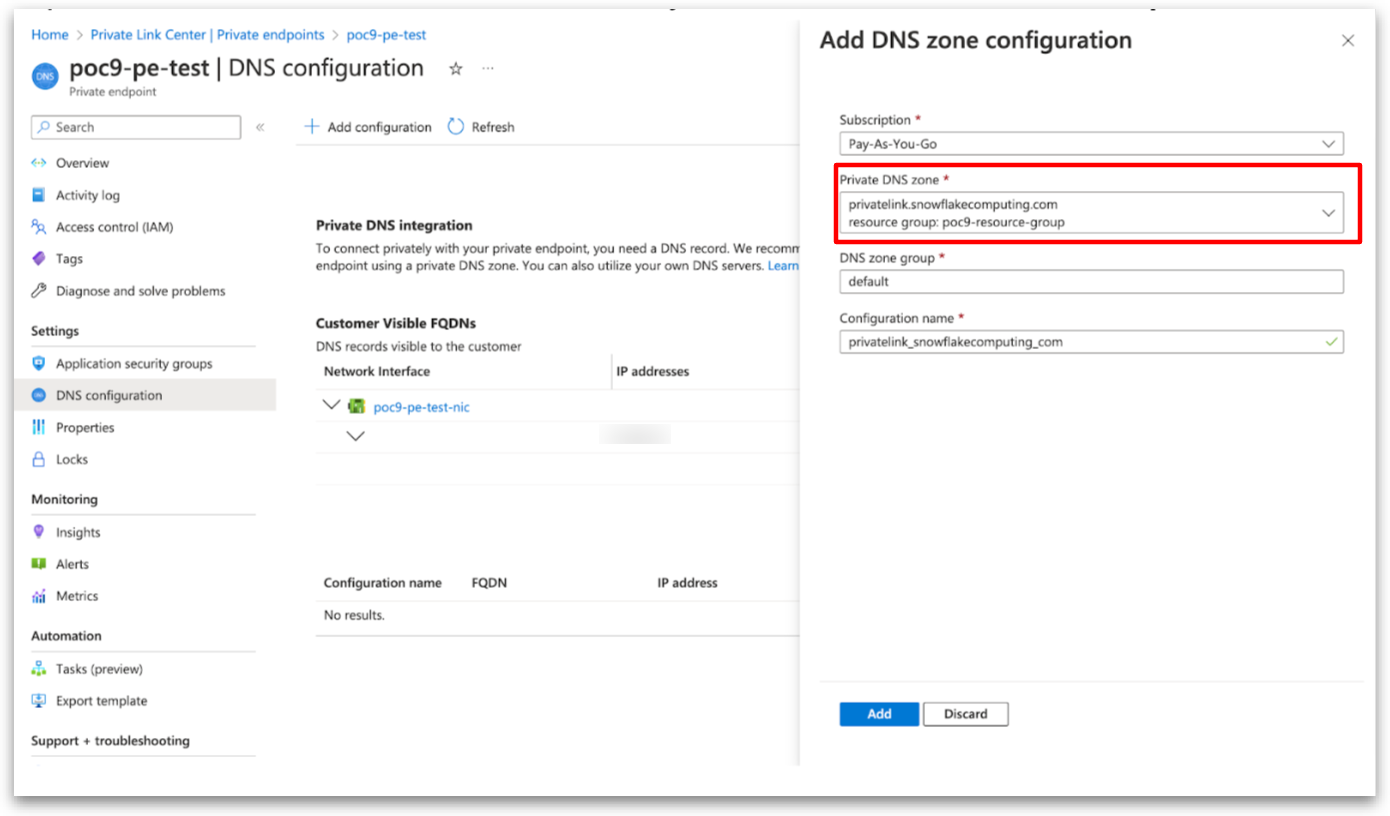
Create Private DNS Zone in Azure
Add Record Sets to Private DNS Zone
Test the Private Link Connection
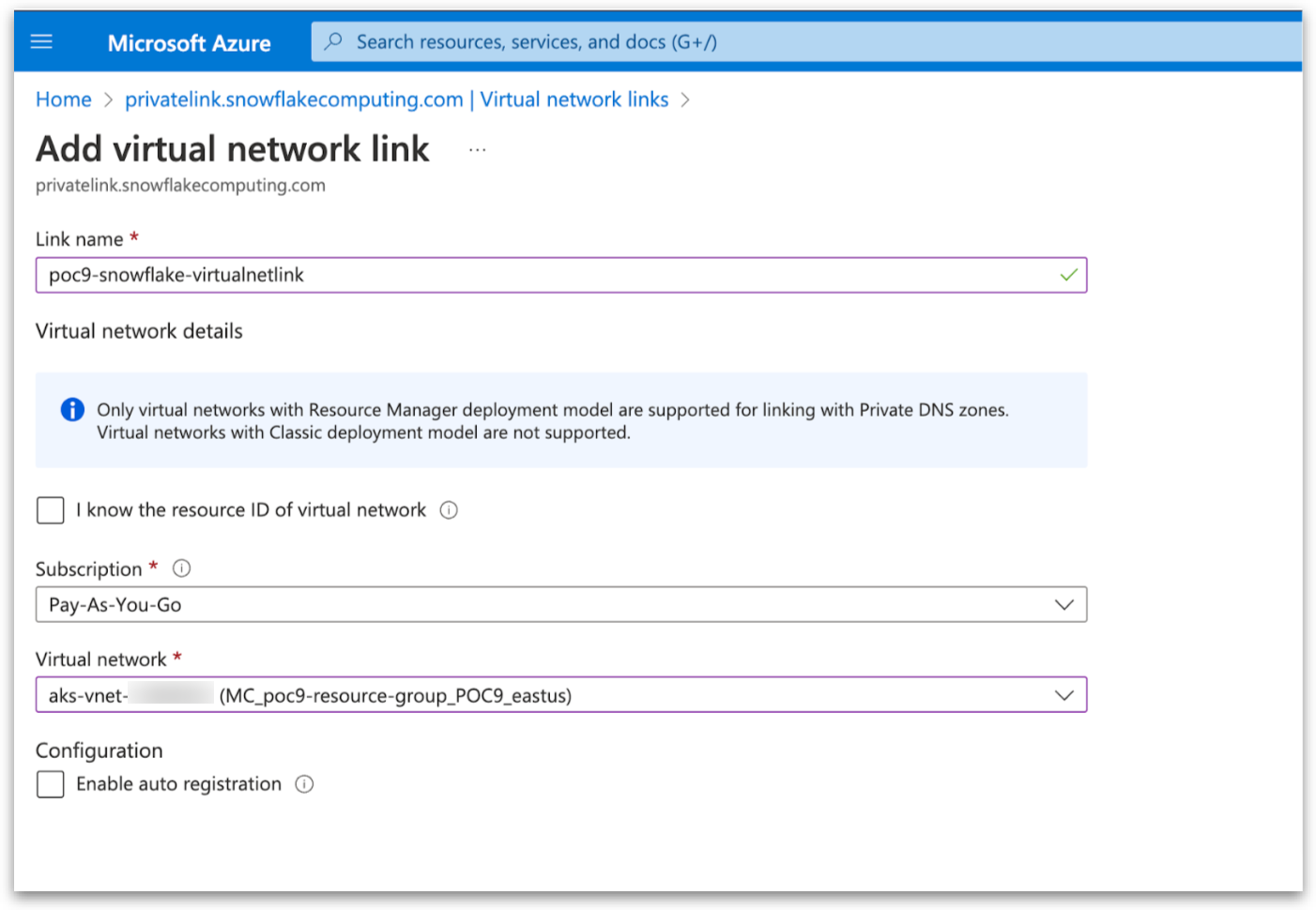
Add the Virtual Network links to the Private DNS Zone
Reference
Was this helpful?