Integrating Snowflake with Okta via OAuth
Integrate Okta with Tellius for Snowflake using OIDC. Follow this guide to configure apps, scopes, claims, and OAuth settings for secure authentication.
1. Navigating to the Okta Admin Page
2. Creating a New Application
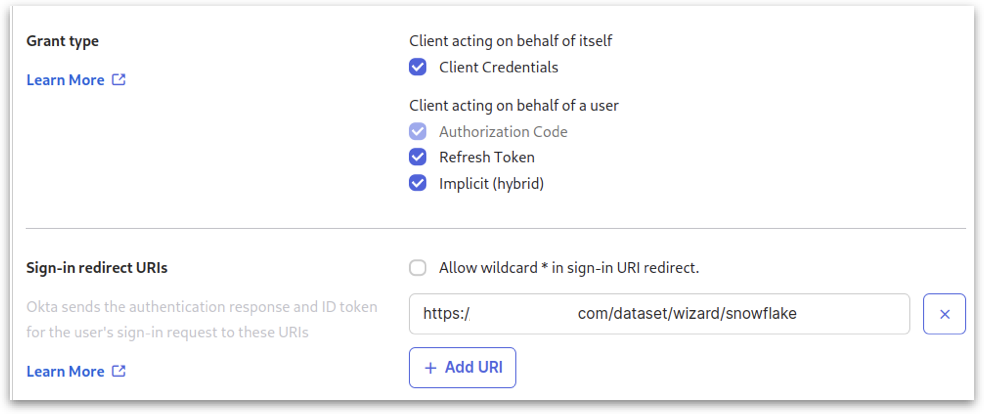
3. Configuring Application Settings
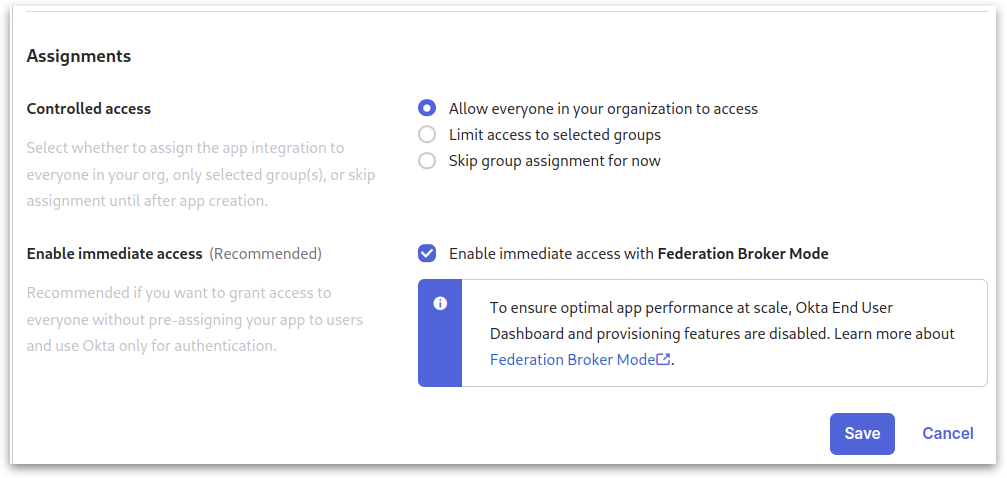
4. Assignments and Saving
5. Getting Client ID and Secret
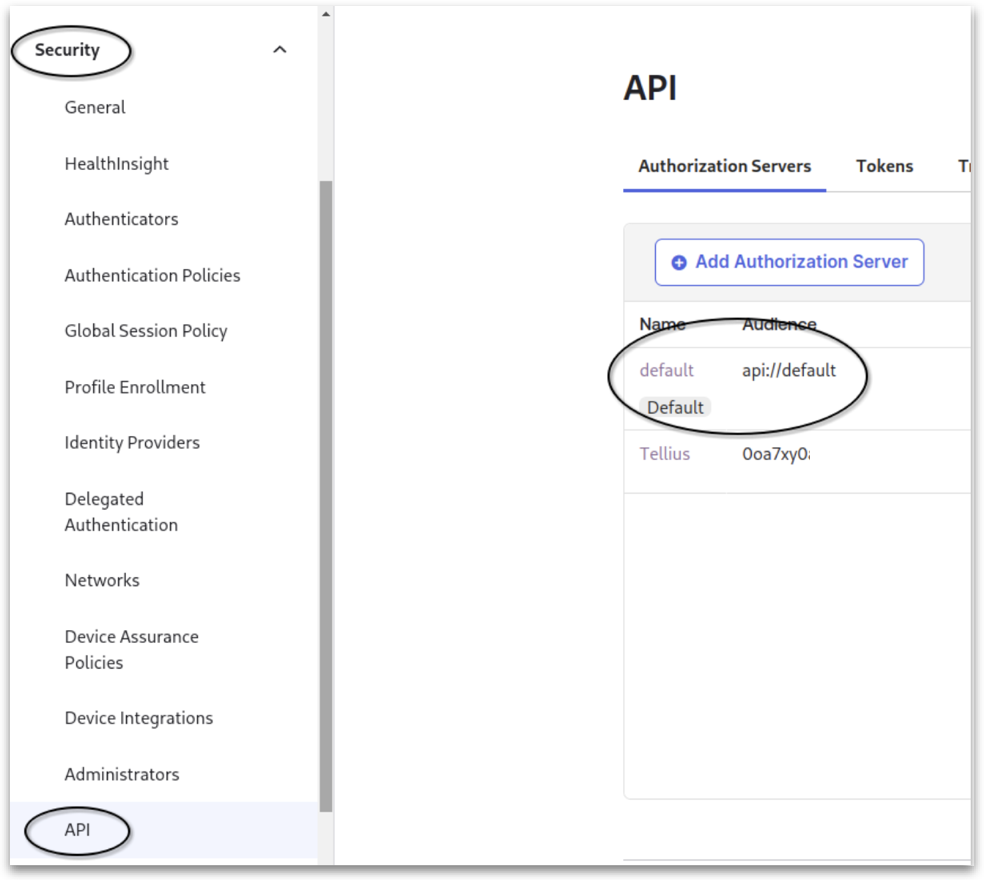
6. Setting Up Security API
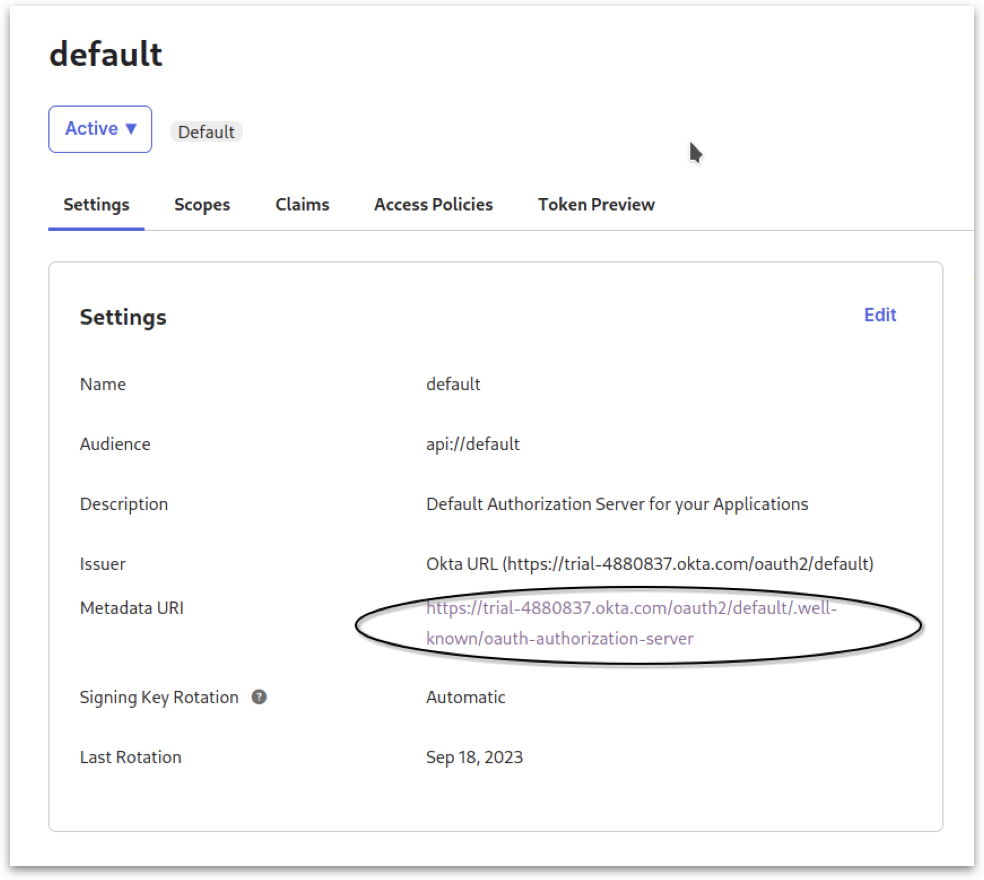
7. Configuring Scopes and Claims
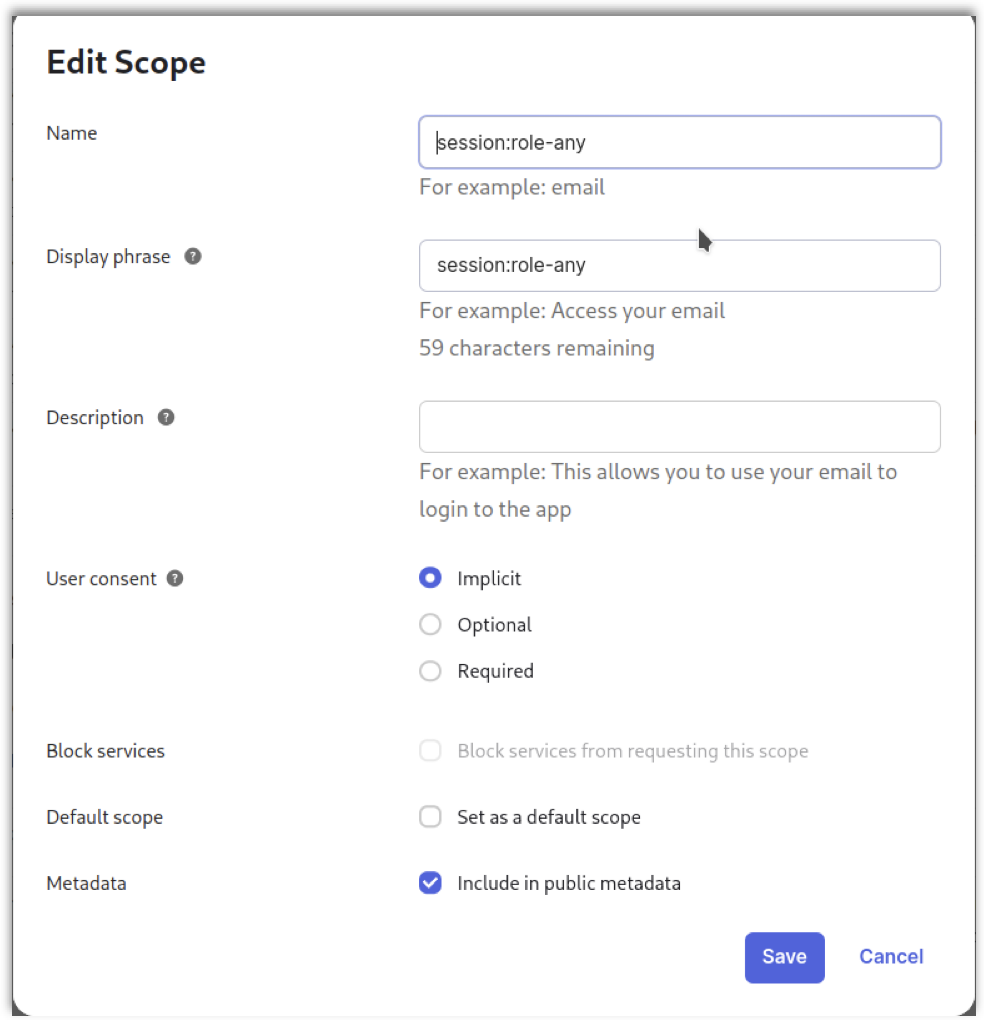
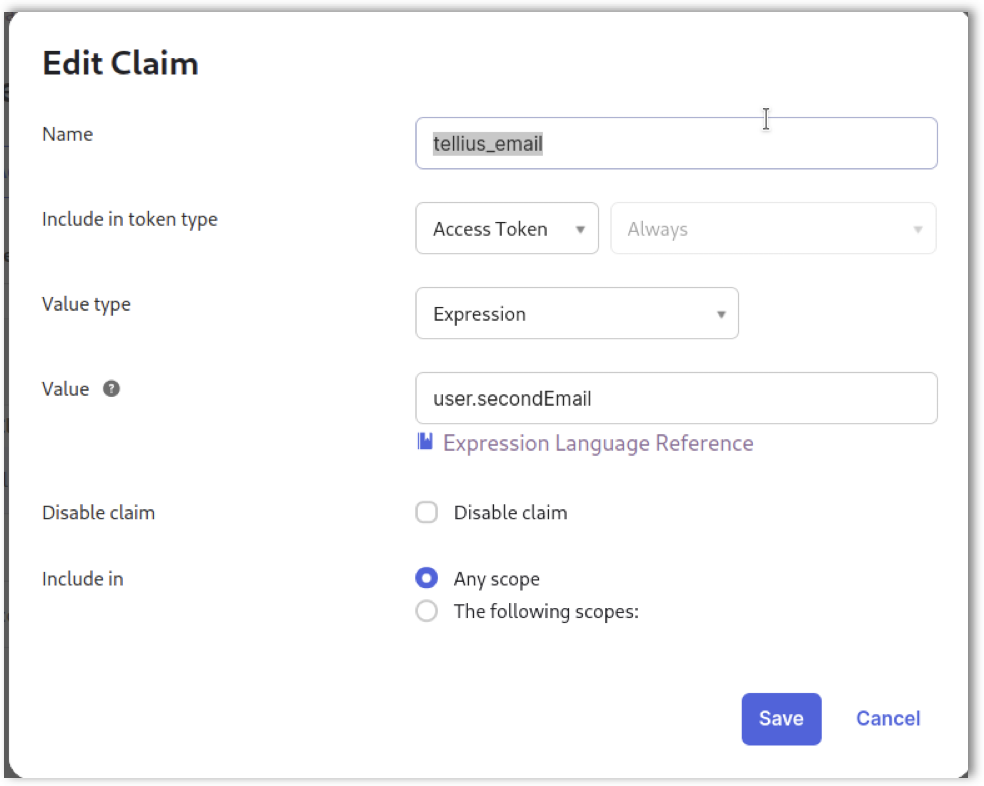
8. Updating User Settings
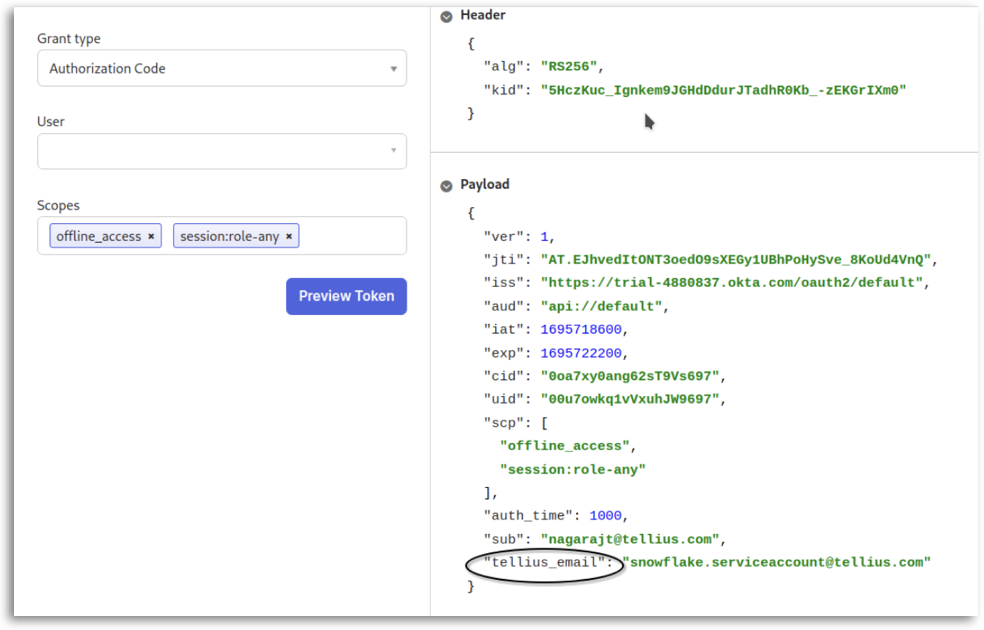
9. Configuring Snowflake Console
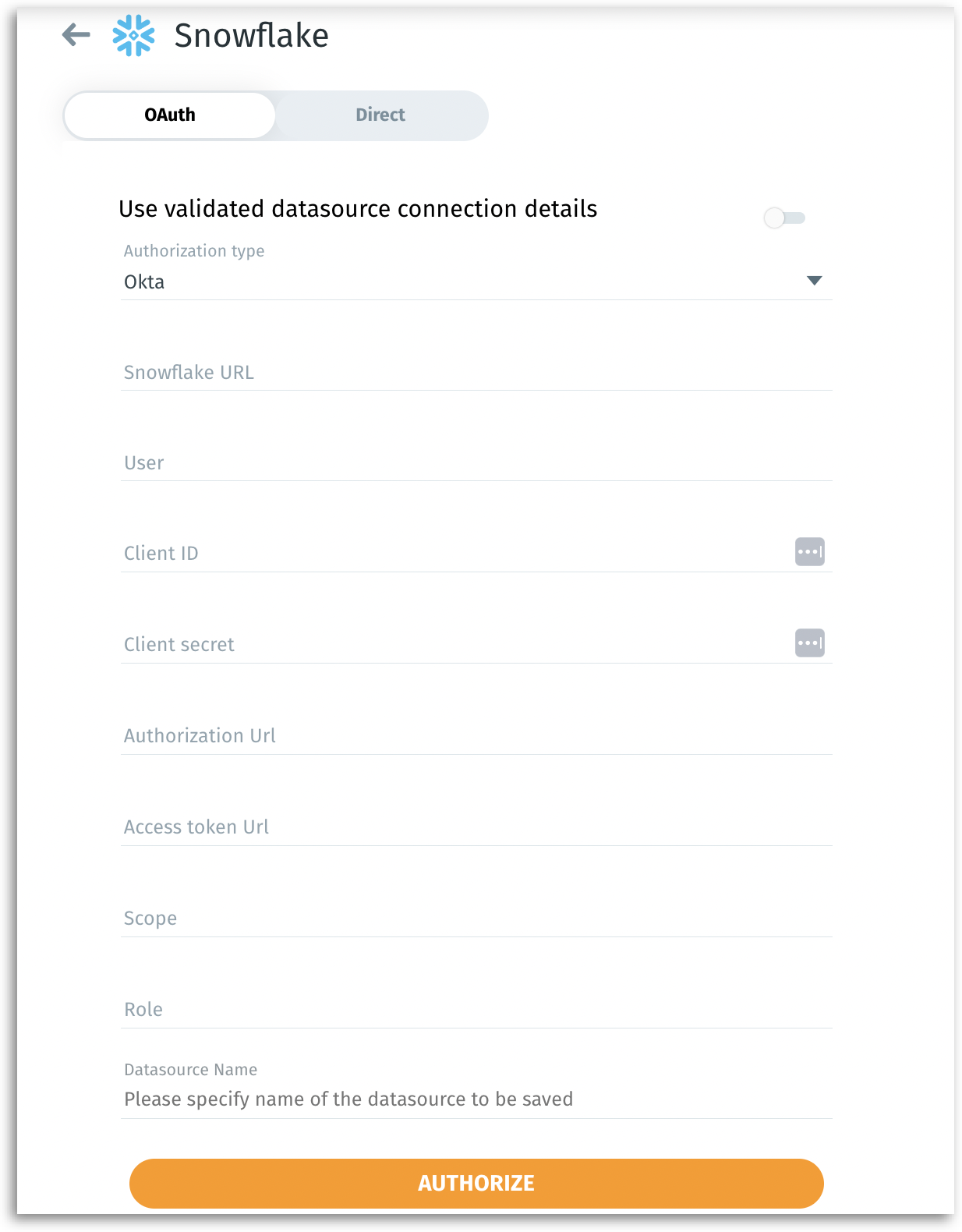
10. Connecting to Tellius
Was this helpful?