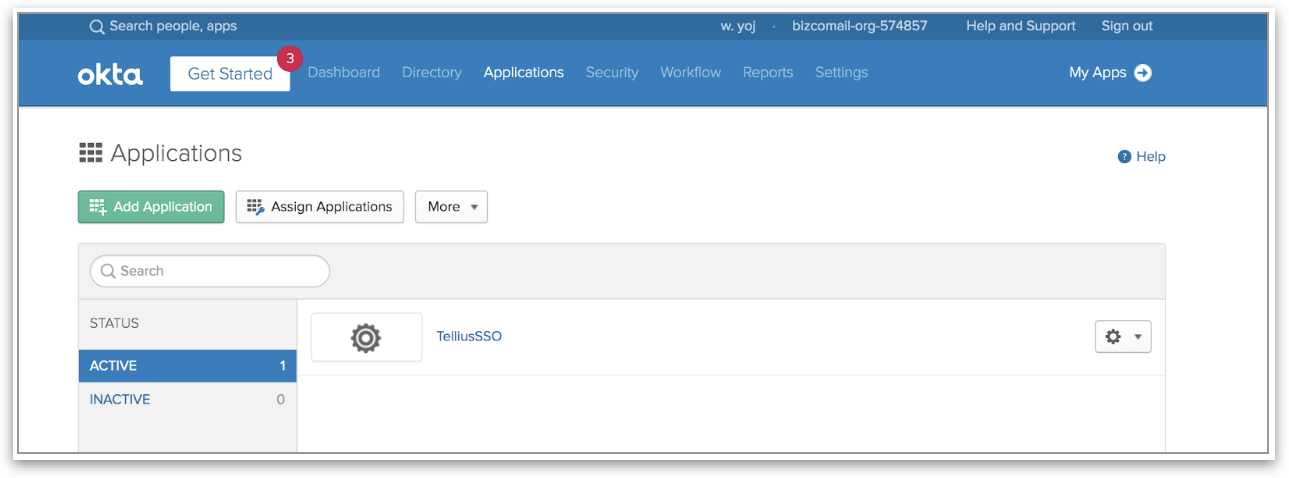
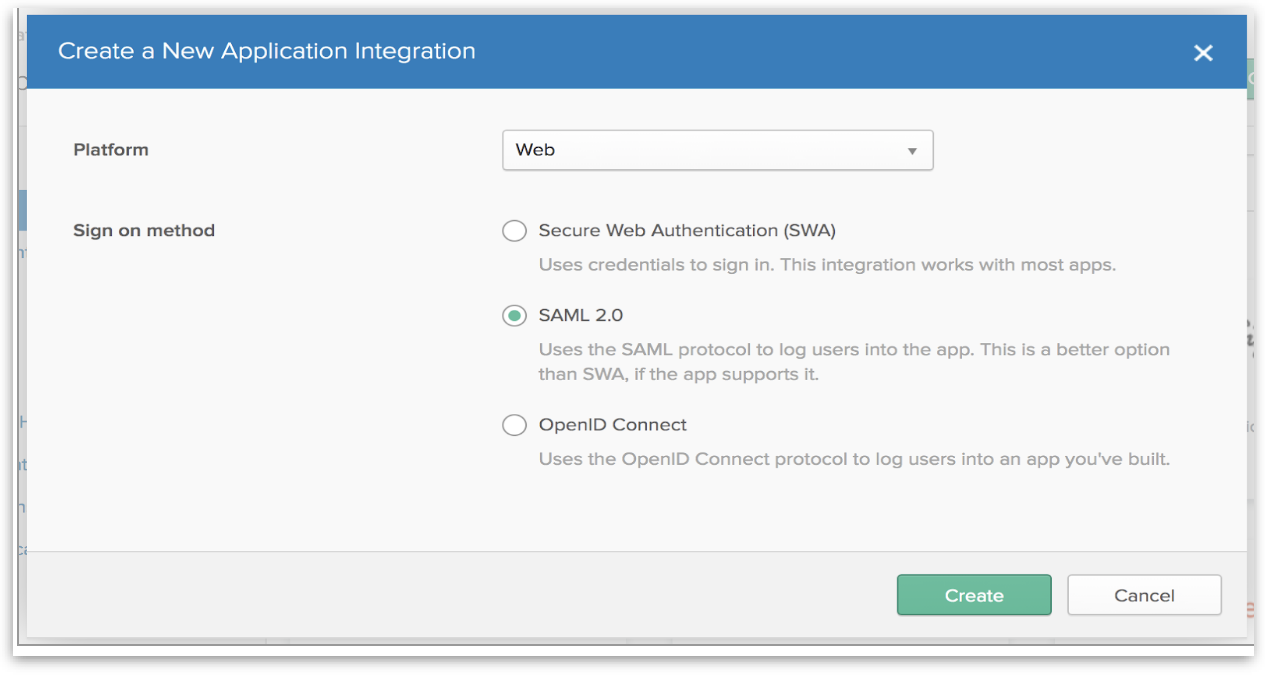
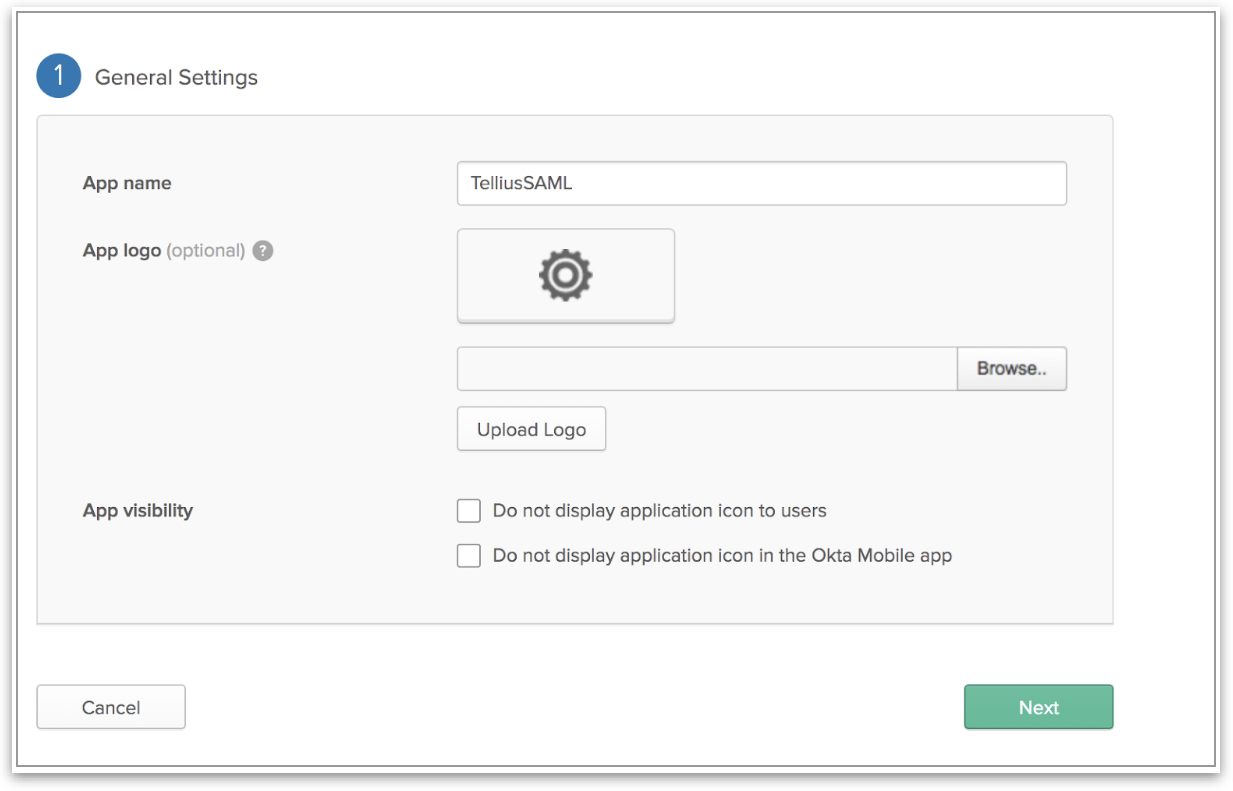
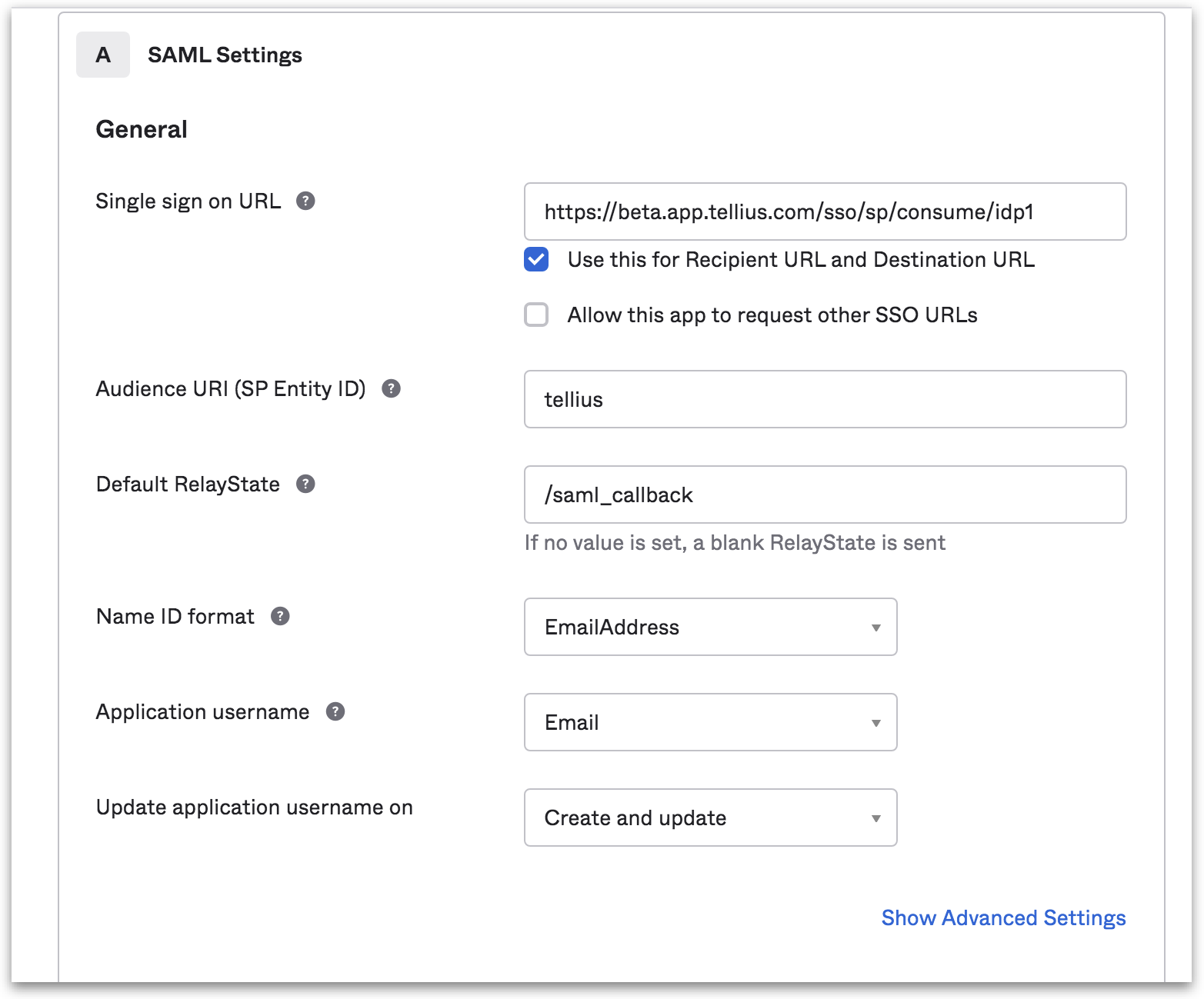
Using Okta as an IdP (SAML Integration)
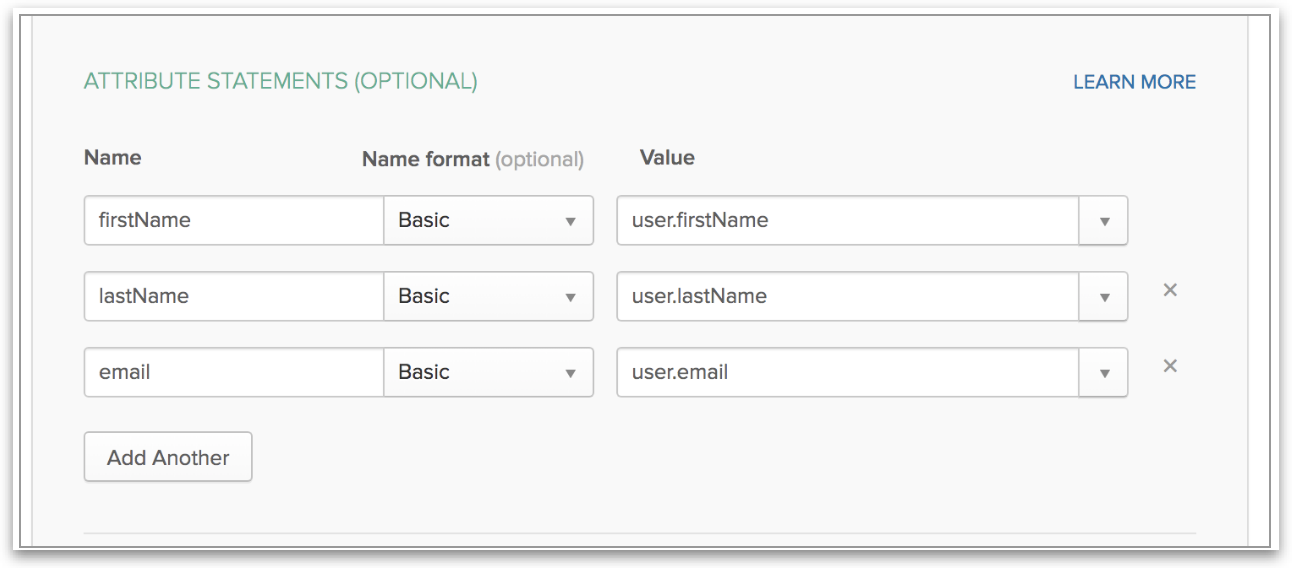
Enable secure SSO for Tellius with Okta. Learn how to configure Okta as your SAML Identity Provider to streamline login and automatically provision users using corporate credentials.
Was this helpful?
Enable secure SSO for Tellius with Okta. Learn how to configure Okta as your SAML Identity Provider to streamline login and automatically provision users using corporate credentials.






Was this helpful?
Was this helpful?